Generate Public Key Ssh Tectia
Invoke the ssh-keygen utility to generate the OpenSSH public/private key pair. In this example, the private key is stored in file identity and the public key is stored in file identity.pub. Note: The -b option specifies the number of bits in the key to create. The SSH server determines the length of the keys. In the example above, the private key file is iddsa2048a. The public key file is iddsa2048a.pub, and it can be distributed to other computers. By default, ssh-keygen-g3 creates a 2048-bit DSA key pair. RSA keys can be generated by specifying the -t option with ssh-keygen-g3. Jun 26, 2019 ssh-keygen -b 4096 The -b flag instructs ssh-keygen to increase the number of bits used to generate the key pair, and is suggested for additional security. Press Enter to use the default names idrsa and idrsa.pub in the /home/yourusername/.ssh directory before entering your passphrase. Generating Keys for SSH Tectia. Let’s look at actually using Tectia for key management. First we generate a key, in our example our user will be “sftpuser.
Bluehost Web Hosting Help
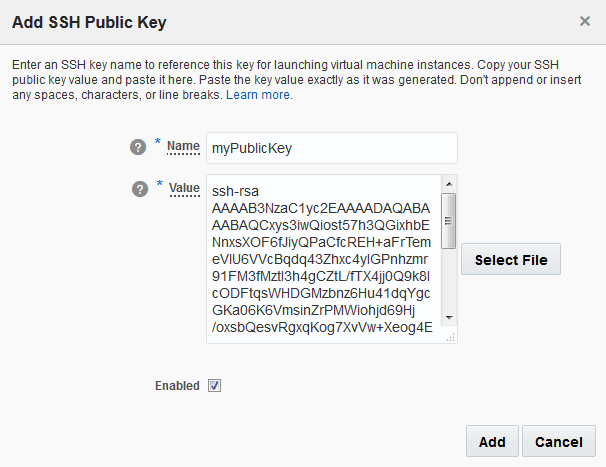
Using a Public/Private key to authenticate when logging into SSH can provide added convenience or added security. The Public/Private key can be used in place of a password so that no username/password is required to connect to the server via SSH. Instead the unique public and private key provide the secure authentication. It is advised that the key uses a different password from your cPanel password.Generating the Key
- Login to your Bluehost Control Panel
- Choose SSH / Shell Access, in the Security section.
- Click Manage SSH Keys
- Choose to Generate a new Key
- Enter a new Key password.
- Choose DSA or RSA for the type.
<=' span='> It is recommend that you choose RSA. - Choose a Key size, it is recommend to use 2048 or higher.
- Click Generate Key
- Click the Go Back button.
Authorize the Key
Authorizing the key will add the public key to the authorized_keys file.- Click Manage Authorization
- Click the Authorize button for your newly created key.
- Click Go Back to return to the main page.
What Is Public Key
Private Key
The private key needs to be stored on your local computer.Tectia Generate Public Key
- To the right of your private key, click View/Download.
- Click the Download Key button to download the private key.
- If on Linux or Mac OS copy the id_dsa file to your ~/.ssh folder.
- On Windows you will want to move it some place safe.
Using your new key
Windows
For Windows please see Using SSH on Windows (PuTTY)Generate Ssh Key
Linux or Mac OS
- Open your Terminal
- Enter the following command
- If you created a passphrase you might see something like the following
ssh username@IPEnter passphrase for key '~/.ssh/id_dsa':Recommended Help Content
Related Help Content
- Using the Authorization File
- Using Keys Generated with OpenSSH
- Special Considerations on Windows
- Authorized Keys on a Windows Network Drive
Public-key authentication is based on the use of digital signatures and provides very good authentication security. To use public-key authentication, the user must first create a key pair on the client, and upload the public key to the server.
Do pc game key generator 2018. The default directory where Tectia Server stores the users' public keys is $HOME/.ssh2/authorized_keys on Unix, and %USERPROFILE%.ssh2authorized_keysIspring for mac free download. on Windows. The directory can be changed with the authorized-keys-directory attribute in the ssh-server-config.xml file. See auth-publickey.
The user is required to have the read rights, (and optionally the write rights) to the public-key files and directories, but the locations must not be accessible to other users. The read permissions are required for the key.pub file, the authorized_keys directory, and to the authorization file, if used. The write permission to these files are needed if the users are allowed to upload their own keys to the server.
To enable public-key authentication on the server, the authentication-methods element of the ssh-server-config.xml file must contain an auth-publickey element. For example:
Also other authentication methods can be allowed.
By using selectors, it is possible to allow or require public-key authentication only for a specified group of users. See Using Selectors in Configuration File for more information.
Using the Tectia Server Configuration tool, public-key authentication can be allowed on the Authentication page. See Authentication.
Copyright 2018 SSH Communications Security Corporation
This software is protected by international copyright laws. All rights reserved.
Contact Information