System.security.cryptography.aes Generate Random Key
- System.security.cryptography.aes Generate Random Key Free
- Steam
- Computer Security And Cryptography
- Random Key Steam
- Python Cryptography Aes
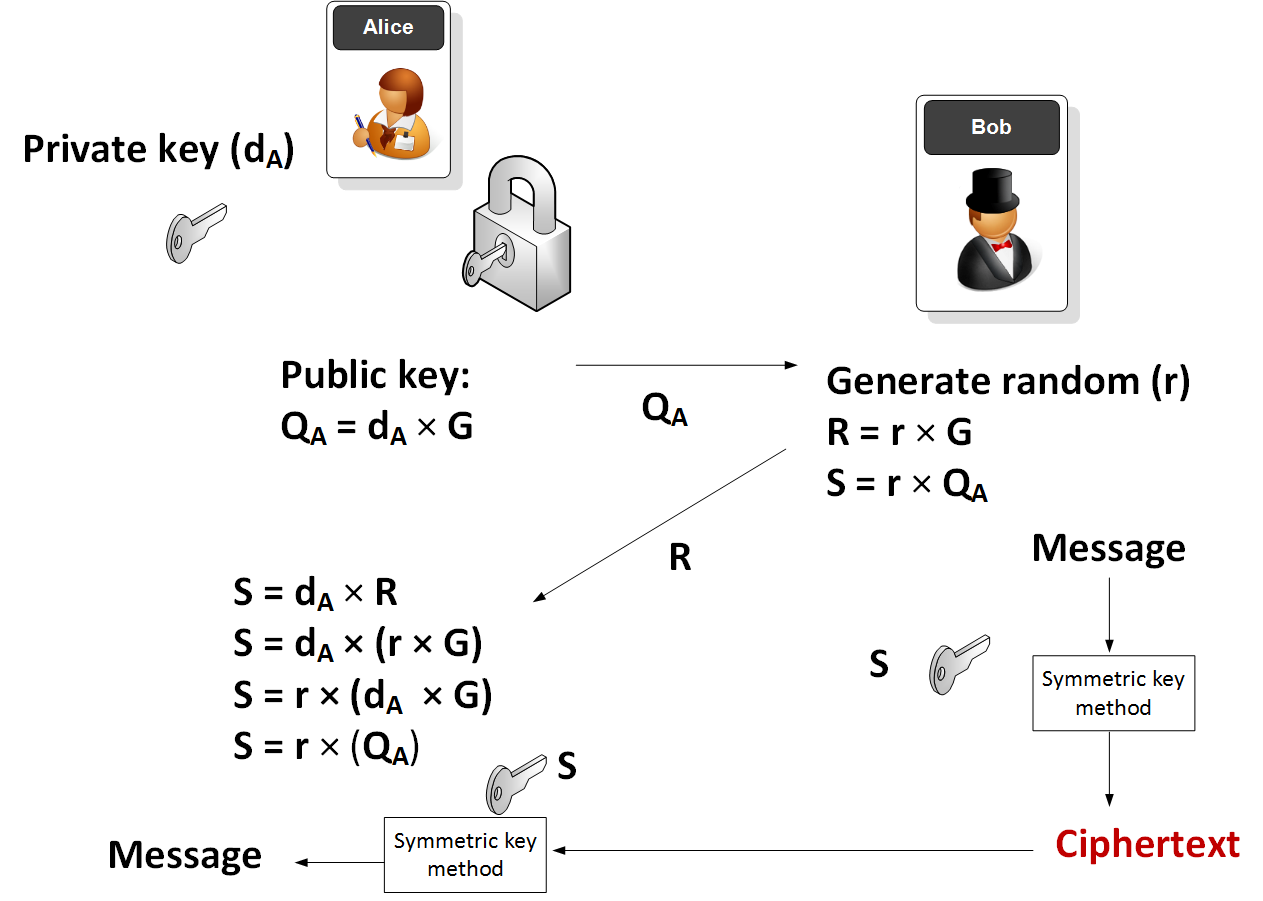
Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
Symmetric Keys
Random String Generator. This form allows you to generate random text strings. The randomness comes from atmospheric noise, which for many purposes is better than the pseudo-random number algorithms typically used in computer programs. // Import the key, then close any current key and replace with the new one. We need to make We need to make // sure the import is successful before closing the current key to avoid having an algorithm. Dec 31, 2014 I was looking for some simple examples of using AES symmetric encryption to encrypt and decrypt data in C#. Though there are some very helpful resources out there, what I needed were basic routines that: - Take clear text and key as byte arrays and return encrypted text as a byte array.
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
- Strong Password Generator to create secure passwords that are impossible to crack on your device without sending them across the Internet, and learn over 30 tricks to.
- AES encryption/decryption using pure.NET and streams. Ask Question Asked 3 years. I've read that it's good practice to generate a random key. If I do that, then both the server and the client would need to know the same key. Using aes As System.Security.Cryptography.Aes = System.Security.Cryptography.Aes.Create, unencryptedStream As.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.
See also
-->Definition
Represents the abstract base class from which all implementations of the Advanced Encryption Standard (AES) must inherit.
- Derived
Examples
The following example demonstrates how to encrypt and decrypt sample data by using the Aes class.
Constructors

| Aes() | Initializes a new instance of the Aes class. |
System.security.cryptography.aes Generate Random Key Free
Fields
| BlockSizeValue | Represents the block size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| FeedbackSizeValue | Represents the feedback size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| IVValue | Represents the initialization vector (IV) for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| KeySizeValue | Represents the size, in bits, of the secret key used by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| KeyValue | Represents the secret key for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalBlockSizesValue | Specifies the block sizes, in bits, that are supported by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalKeySizesValue | Specifies the key sizes, in bits, that are supported by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| ModeValue | Represents the cipher mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| PaddingValue | Represents the padding mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
Properties
| BlockSize | Gets or sets the block size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| FeedbackSize | Gets or sets the feedback size, in bits, of the cryptographic operation for the Cipher Feedback (CFB) and Output Feedback (OFB) cipher modes. (Inherited from SymmetricAlgorithm) |
| IV | Gets or sets the initialization vector (IV) for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| Key | Gets or sets the secret key for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| KeySize | Gets or sets the size, in bits, of the secret key used by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalBlockSizes | Gets the block sizes, in bits, that are supported by the symmetric algorithm. |
| LegalKeySizes | Gets the key sizes, in bits, that are supported by the symmetric algorithm. |
| Mode | Gets or sets the mode for operation of the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| Padding | Gets or sets the padding mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
Methods
| Clear() | Releases all resources used by the SymmetricAlgorithm class. (Inherited from SymmetricAlgorithm) |
| Create() | Creates a cryptographic object that is used to perform the symmetric algorithm. |
| Create(String) | Creates a cryptographic object that specifies the implementation of AES to use to perform the symmetric algorithm. |
| CreateDecryptor() | Creates a symmetric decryptor object with the current Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateDecryptor(Byte[], Byte[]) | When overridden in a derived class, creates a symmetric decryptor object with the specified Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateEncryptor() | Creates a symmetric encryptor object with the current Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateEncryptor(Byte[], Byte[]) | When overridden in a derived class, creates a symmetric encryptor object with the specified Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| Dispose() | Releases all resources used by the current instance of the SymmetricAlgorithm class. (Inherited from SymmetricAlgorithm) |
| Dispose(Boolean) | Releases the unmanaged resources used by the SymmetricAlgorithm and optionally releases the managed resources. (Inherited from SymmetricAlgorithm) |
| Equals(Object) | Determines whether the specified object is equal to the current object. (Inherited from Object) |
| GenerateIV() | When overridden in a derived class, generates a random initialization vector (IV) to use for the algorithm. (Inherited from SymmetricAlgorithm) |
| GenerateKey() | When overridden in a derived class, generates a random key (Key) to use for the algorithm. (Inherited from SymmetricAlgorithm) |
| GetHashCode() | Serves as the default hash function. (Inherited from Object) |
| GetType() | Gets the Type of the current instance. (Inherited from Object) |
| MemberwiseClone() | Creates a shallow copy of the current Object. (Inherited from Object) |
| ToString() | Returns a string that represents the current object. (Inherited from Object) |
| ValidKeySize(Int32) | Determines whether the specified key size is valid for the current algorithm. (Inherited from SymmetricAlgorithm) |
Steam
Explicit Interface Implementations
Computer Security And Cryptography
Random Key Steam
| IDisposable.Dispose() | Releases the unmanaged resources used by the SymmetricAlgorithm and optionally releases the managed resources. (Inherited from SymmetricAlgorithm) |